
There is an old saying in poker, "If you can't spot the sucker in the first half hour at the table, then you ARE the sucker." The same goes for CFOs. If you cannot identify your company's security weaknesses, then you are the weakness.
CFOs are not the first executive that comes to mind when discussing the topic of cyber security. Mostly this is a CIO or CTO responsibility. However, CFOs play a critical role in the conversation as security breaches pose a significant risk to the overall business from financial transaction data leaks to operational and reputation management. Without the proper guardrails, chaos could quickly ensue, affecting the bottom line, which is important to all leaders and team members alike but ultimately the CFO’s responsibility. Therefore, CFOs must take a seat at the table when it comes to cyber security.
Here are three common incidents that will happen to you:
- User accounts on social media, particularly professional networking channels like LinkedIn, are susceptible to breaches. Organizations encourage employees to leverage LinkedIn for thought leadership sharing, sales and marketing, and business development. It is not uncommon for these accounts to be infiltrated and used to send out password phishing messages.
- Another example is when cyber criminals create and distribute very realistic email messages to internal users at a company. These messages may appear to come from the company’s email platform account like Microsoft indicating that the user’s email account storage is full.
- Finally, one important example specifically to CFOs or other financial leaders in organizations is AI (Artificial Intelligence) impersonating the voices of people and using that to obtain credit card information. This is particularly disconcerting as it has a direct impact on the financial security of the company.
CFOs must be aware of the following risks and safeguard staff and management with access or authority to company financial information.
Here are several tips CFOs and financial leaders can share with their staff to protect the organization from threats:
- Account security. For the most critical accounts, LinkedIn, email, banking, etc., use two-factor authentication at a minimum to access these accounts. Two-factor authentication sets a standard for user log-ins. It texts a six-digit number, which must be entered to gain access to the account. This is a simple way to prevent account hacking. Users can expand the functionality for their more sensitive accounts by using an authenticator app on their smartphones.
- Password choice. It was once recommended that users change their passwords often and choose very difficult passwords. Recently the advice has changed. The recommendation now is to combine three common words with a couple of numbers, and instead of changing it often, it is recommended that you have a different password and never use the same password twice. For example, the password “3b99DgZz%UIP29SxAqU8&lV!x,” is difficult to remember and use but “BarnTempLose42” is just as good and easier to remember. The reason users should not have the same password for multiple online accounts is that some phishing attempts will gain one password and within two seconds, have tried it on multiple sites.
- Password storage. Most users will ask, “How do we remember long passwords or separate passwords for all of my websites?” One program to alleviate this burden is called LastPass – a password management tool. Our techy CFOs recommend it and there are others, like Dashlane. These tools have enterprise options to securely share passwords among employees.
- Attachments and fake emails. These threats are on the rise and require careful attention. Here are several rules of thumb to apply in managing email accounts:
- If the attachment is an HTML file, do not open it. Delete it right away or send it to your IT manager. There are very few reasons anyone should be sending users an HTML file.
- If the attachment is a PDF, it is relatively safe to open. However, if it is not legitimate it will ask you to click on it to go to a website which is the same as an HTML file. It is suggested to not click on it and delete it.
- If the email comes from a Gmail account or a similar free account but says Microsoft or DocuSign for example, immediately delete it.
- If it looks legitimate and the user is interested in what the message is saying, the user should always go to the source to check it out rather than clicking on the email itself. For example, if the email says it is from Microsoft or DocuSign, users should type microsoft.com or docusign.com in their search engine and log into their account without clicking on an attachment or following a link as that is laced with risk.
- Have a designated cyber security or IT manager for the organization. Users should be encouraged to call or send questionable email messages to this “emergency contact” to determine if the message is legitimate or not.
- If a user clicks on something, enters their password, and then realizes what happens, they should contact the organization’s cyber security leader right away. The designated “emergency cyber security partner” will help the user change their password to the specific account and log everybody out so they’re protected. However, going full circle to the note on number one above is if you have two-factor authentication - odds are, even if the hacker obtains the user’s password, they cannot get into the account.
- Here is an example of an HTML file attachment.
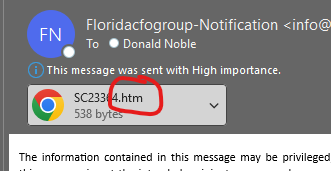
- New scamming techniques. Cyber criminals are now using Artificial Intelligence to mimic a person’s voice to get information. Recent reports show a newscaster’s voice being imitated as him calling his mother to obtain her driver's license information. Fairly innocuous, however, other reports show the mimicking of a CFO's voice to ask an employee for credit card information, then again asking the employee to purchase gift cards. Even more disturbing was that the conversation was interactive. This means that when the person asked a question, the Artificial Intelligence responded. All CFOs and financial leaders ought to be aware of this type of fraud to protect their companies. Read more about this type of scam published by The Conversation and watch the CBS News report.
For more information regarding CFOs on cyber security, contact Florida CFO Partner, Don Noble.